
How to Scale Your Cybersecurity With Your Business
As your company evolves from startup to growth stage, cybersecurity needs to follow along to support, or perhaps even lead, the business.
First, you need to hire a great leader to own the strategy, then you need to build a security architecture to support the growth they create. Here, we’ll focus on the final step of the journey and by far the most challenging one: scaling your security strategy as your business reaches late-stage and starts preparing for an exit or IPO.
I was lucky enough to lead cybersecurity at a multi-billion dollar public company that achieved tremendous success, faced seemingly insurmountable challenges, and leveraged its security leadership to effectively reinvent itself. I now advise Georgian companies on how to build out their architectures as they raise hundreds of millions of dollars, achieve unicorn status, get acquired by some of the world’s top tech firms, or even decide to go public themselves.
These incredible outcomes have taught me a lot about what to do (and what not to do) as businesses grow, and I’d like to share some of these learnings to try and help guide you on your own journey.
Benchmark Your Security
One of the most challenging aspects of cybersecurity is measuring it. As much as we’d love to have a single, objective way of measuring risks, mitigations and ROI of security investments that applies to all (or even most) environments, it simply doesn’t exist.
So how do you benchmark something that can’t be perfectly measured? You start with an imperfect measure, accept its limitations and iterate to improve over time. The most common ways to do this include:
- Leveraging industry standards such as MITRE ATT&CK or the CSA CAIQ to map out your controls and highlight threats and opportunities.
- Investing in third-party risk management platforms such as UpGuard, BitSight or SecurityScorecard to measure your partners, your competitors and, of course, yourself.
- Creating your own framework to match your unique business needs, environment and perspectives (for example, we created the Georgian Trust Framework to reflect our view of security as a key ingredient for building and leveraging customer trust).
Industry standards tend to be very comprehensive, but you might find some sections don’t apply to your business and others aren’t fully addressed, so don’t be afraid to adapt the standards as you see fit. Risk management platforms are a great way to get a numerical comparison against your competitors and highlight obvious issues, but they provide an outside-in perspective without understanding the intricacies of your environment or addressing risks such as insider threats. Creating your own framework is obviously the most flexible option, but requires a lot of up-front work and can lead to biased approaches and results.
My advice is to pick one method, learn as much as you can from it, then expand your model as needed. Just like there are many ways to look at financial metrics, there are many ways to measure cybersecurity, and the best way to discover which ones make sense for your business is by trying out different approaches.

Align With The Leadership Team
Once you have a good sense of your cybersecurity strengths and weaknesses, present them along with a set of key recommendations to your leadership team. Depending on your role and organization, these might be your technical managers or C-level executives, but more often than not, cybersecurity is becoming a board-level discussion, even at startup and growth-stage companies.
Be sure to tailor the content to your audience. If you’re presenting to board members who may not have an in-depth understanding of security operations, focus the discussion on high-level risks to the organization from a regulatory, reputational, and of course, financial perspective. If you’re presenting the CTO and engineering teams, you’ll want to go a bit deeper and take them through the methodology and benchmarks that you used to evaluate your security.
Be open, honest, transparent, and, most importantly, factual with your observations. Resist the common urge to paint a rosy picture in order to make yourself and your team look good — this can and likely will backfire when the reality becomes apparent in the future. At the same time, don’t fear-monger to try and get more resources — it might work once or twice, but people will eventually figure out you’re crying wolf and you’ll quickly lose credibility. Your job is to be the messenger of truth, and if the truth isn’t good, then be sure to present a plan on how to make it better.
Last, but definitely not least, remember that these types of discussions can be unpredictable. Some executives will go down rabbit holes asking about specific controls or recent incidents, others will challenge your observations if they don’t fit with their perceptions and others will unexpectedly support your ideas and recommendations. Prepare your facts and reasoning well in advance, do your best to keep the meeting on track while letting everyone have their say, and most importantly summarize the key takeaways verbally at the end of the meeting and in writing afterwards to get everyone aligned on the strategy and next steps.

Grow Your Team With The Organization
As the company grows, you’ll naturally need to build out your own team to support it. How quickly you do this depends on a lot of factors, but a good rule of thumb is to try to grow at a rate slightly below the rest of the company. For example, if the company plans to double in size in the next two years, you’ll probably want to grow your team by about 50-75% in that same timeframe. That makes sure you’re able to effectively support the increased security demands while forcing you to create economies of scale and leverage technologies and automation (more on this later).
The roles you hire and the order you hire them in will depend a lot on your specific needs, which should become obvious through the benchmarking and executive discussions. As you build out the team, you’ll want to hire a mix of security specialists, analysts, managers and architects, along with engineers specializing in different areas (e.g. application security and network security). I generally prefer to start with entry-level roles and add seniority where needed — if you do a great job hiring and nurturing talented people, some will naturally grow into the higher-level roles that you’ll need down the road.
As the CISO of one of our companies pointed out, a lot of the principles of hiring your first security leader apply to the rest of the hires as well. Where possible, focus on one role at a time and prioritize intelligence, personality, initiative and intellectual curiosity over specific skills and experience that are needed in the short-term. Take your time finding the right candidate and make sure they’re just as excited about joining as you are to have them on board.
Ineffective security leaders often view hiring as a distraction from their day-to-day work and try to offload the task of finding, evaluating and even onboarding new employees to HR or others in the organization. This can lead to bad hires who end up creating more problems than they fix and teams that lack cohesion, thus creating exponentially more work for the leader. For any type of executive leader (not just within cybersecurity), the single most effective way to help your business long-term is by finding, hiring, growing and retaining top-notch industry talent.

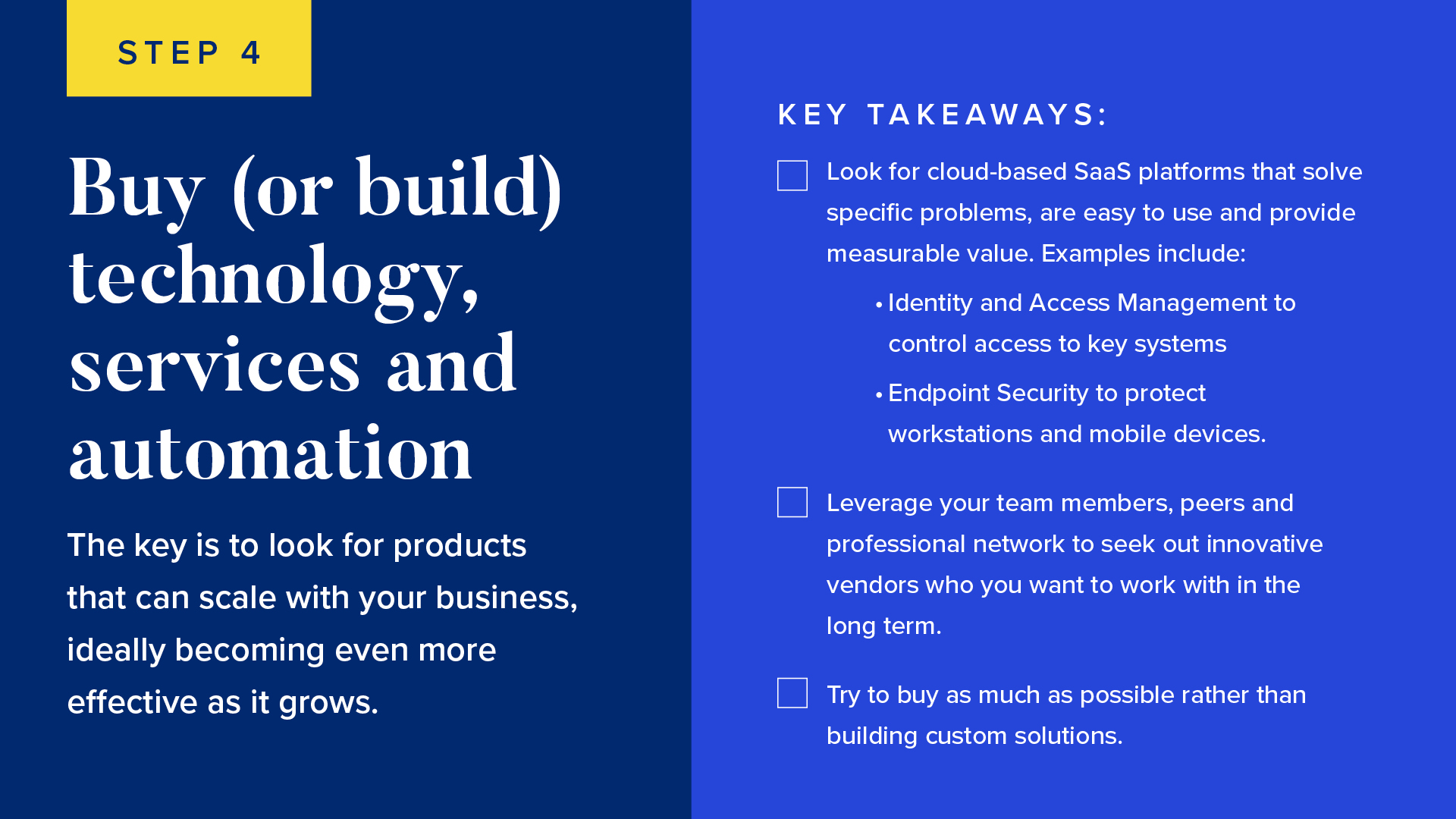
Buy (or Build) Technology, Services and Automation
As you start hiring the right people, be sure to give them the tools they need to do their work. The key is to look for products that can scale with your business, ideally becoming even more effective as it grows. Look for cloud-based SaaS platforms that solve specific problems, are easy to use and provide measurable value. Examples include:
- Identity and Access Management to control access to key systems
- Endpoint Security to protect workstations and mobile devices
- Cloud Security to manage your cloud deployments
- Network Security to prevent and detect intrusions
- Web Security to protect your online properties
- Security Incident and Event Management to track and resolve issues
- Managed Detection and Response to outsource and/or provide additional inputs
- Security Orchestration, Automation and Response to bring everything together
Leverage your team members, peers and professional network to seek out innovative vendors who you want to work with in the long term. Look for partners that not only provide great software, but also great customer service. Value references from people you know, take sales pitches with a grain of salt and trust your gut reaction to demos and proof of concepts.
Last but not least, try to buy as much as possible rather than building custom solutions. Some organizations fall into the trap of trying to build nearly everything themselves, thinking they can create better products than the likes of Google or Microsoft (spoiler: they usually can’t). Most security platforms are much more complex than they appear, and specialized vendors often have tremendous industry knowledge and economies of scale that are very difficult to replicate. If your firm sells cybersecurity solutions, then by all means be sure to leverage them internally; otherwise, my advice is to trust the experts.
Always Keep Learning and Evolving
Remember that cybersecurity is a journey, not a destination. Perfect security is an asymptote and your job isn’t to protect the business against all threats; it’s to create value by mitigating risks and ensuring your customers trust your company and products. In order to do this effectively, you’ll need to constantly monitor, refresh and upgrade your architecture as your business changes and evolves over time.
Humility is one of the keys to long-term success in all aspects of business and life, especially in a cat-and-mouse game like cybersecurity where you need to accept the unfortunate fact that you’re not the cat. No matter how great of a job you do, there will always be new technologies, new threats, new threat actors and new attacks that you’ll need to address. Some see this as a bug, but I think it’s actually the single greatest feature of cybersecurity. There aren’t many industries where you can work for decades and still learn new things every day, but cybersecurity is certainly one of them.
Next Steps
This wraps up our three-part series on cybersecurity for startups, from hiring your leader to building your architecture to scaling your business. Now that we’ve laid the foundation, we’re ready to start digging into more technical, contemporary and even futuristic areas, from dealing with online misinformation to leveraging machine learning, to the long-term threats and opportunities of IoT and quantum computing.
If any of these topics sound particularly interesting or if there are others you’d like to learn about, please let us know on social media or contact me directly on LinkedIn. And as always, stay alert, stay safe, and most of all stay healthy.
Read more like this
Testing LLMs for trust and safety
We all get a few chuckles when autocorrect gets something wrong, but…
Introducing Georgian’s “Crawl, Walk, Run” Framework for Adopting Generative AI
Since its founding in 2008, Georgian has conducted diligence on hundreds of…